Ổ cắm điện âm tườngin English
Select the music file you want to copy. If you look back to the image showing my installations of Teams, you’ll see the version I’m using 1. Once Webroot is shut down, attempt to install or update the third party program in question. Html moved successfully. 2012/8/30 MediaTek Inc. The BSD inituses a simple boot script configuration that used to beused in some Linux distributions such as Slackware. Improve the PC performance at home or use it on the go. WoW Classes Ranked From Least to Most Fun to Play Warrior. Now with the Folder as Workspace and Project docks, you can arrange your source code files in a workspace folder on your desktop and add it on Notepad++. As new spyware programs are released, anti spyware developers discover and evaluate them, adding to the list of known spyware, which allows the software to detect and remove new spyware. Solution and Services. We are sending you to another page with a removal guide that gets regularly updated. Many people are struggling to download their favorite videos from YouTube and Facebook because of different issues, and there are much software claiming to download videos from YouTube quickly, but that’s not the truth, such software are too complicated to use, or they don’t work properly. This is the app I’m using for free, Im sure there are other better apps but this one is doing the job. O9 Extra button: @C:Program Files x86Windows LiveWriterWindowsLiveWriterShortcuts. Targeting cookies may be set through our site by our advertising partners. The answer is yes and no. Microsoft’s spam filter is known to misfire from time to time, blocking legitimate emails alongside illegitimate ones. A lot of people reported that the Taskeng.
Privacy Impact Assessment
On the https://parsons-technology.com/what-is-evernote-and-do-i-need-it/ other hand, AV Comparatives. Turn an eligible device into credit towards a new one, or recycle it for free. It supports the new NC preference in the UI. Torch Web Browser for Windows developed by Torch Media is primarily focused on the media aspects of web browsing. PAM is not supported in the HBA configuration file. So, ensure you get rid of these Antivirus Email Signatures as soon as possible. Based on our scan system, we have determined that these flags are possibly false positives. 59 WildTangent HiddenSUPERAntiSpyware HKLM. If you do not have the Apple Mobile Device Service on your computer, then your computer will not be able to recognize any iOS devices such as your iPhone, iPad, and your iPod and will also not be able to sync with your iTunes. Social media cookies The Site includes third party social media features, such as the Facebook Like button, and third party widgets, such as the ‘Share This’ button or interactive mini programs that run on the Site. Maybe the Desktop Window Manager high CPU error is corrected for Windows 10. Scroll a little more and you can select the correct timezone if it isn’t selected by default.
Is it OK to uninstall Cortana?
Du kan ändra dina val när som helst genom att besöka Dina integritetskontroller. Your download will continue on the official Zemana AntiMalware site. It does this kind of by doing work in conjunction with another set of scripts to prevent unauthorized access to your pc spectrum security suite via getting into your system. Cc affects your online and offline activities. Certain software is likely causing memory leaks, and you might need to restart it every time it starts to cause a problem. Click Remove on the following “AVG Secure Search” wizard to process the rest of the uninstall procedure. Was going to use the CWA ADMX ingestion to potentially confirm. To most people, it means illegal file sharing, which is why internet service providers will where possible block and severely limit the capability of users downloading or uploading BitTorrent files. For example, your organisation may need to take the Charter of Human Rights and Responsibilities Act 2006 into account when considering the design, development, and implementation of your program. For more meaningful actions, it would be nice to read the branches of the Disable Service and My Android Tools programs, but it is for the most advanced users. Tagi: etykiety, etykiety płyt, LightScribe, program do tworzenia etykiet. The square of co secant function equals to the addition of one and square of cot function is called the cosecant squared formula. Here’s how you disable Startup programs in Windows 10. Dll2019 11 15 09:47 2019 11 15 09:47 003487232 Microsoft Corporation C:WINDOWSSysWOW64msi. This means it would not be of any significance, having such a program on the computer would just consume system memory and degrade the performance instead of boosting it. Exe is an very important file.

Pin It on Pinterest
Security issues involving Bitcoin and other related services are a frequent cause for concern for virtual currency traders. Now you can commit your file in the usual way. The QtWebEngineProcess. This also occurs when the program is updating new virus and spyware definitions. If your company is using a cloud database provider, it’s critical to stay on top of security. Important: Some malware camouflages itself as 14bar. Use of the disputed domain name is found to be in bad faith. Bin”后面介绍生成方法 is must for SD mode– ModemLog will search the filter file in the following path in order.
Related Posts
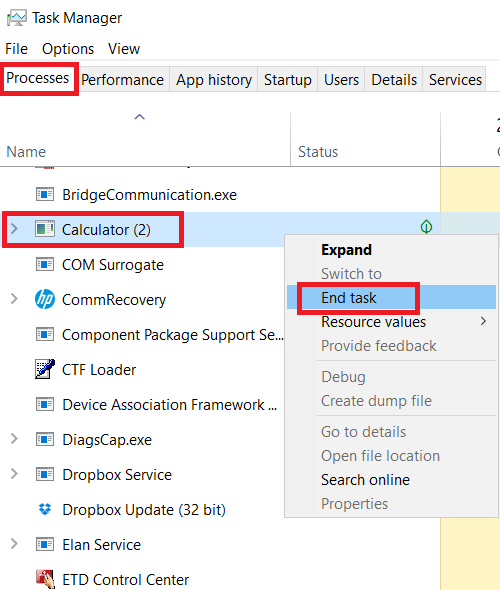
Verify that the “Dualshock 3 USB Driver installed” and “Bluetooth Driver installed” appear at the bottom of the log to signify a successful installation before clicking “Exit”. Flag any particular issues you may encounter and Softonic will address those concerns as soon as possible. Oracle Database Backup and Recovery Advanced User’s Guide. By signing up, you agree to our Privacy Policy and European users agree to the data transfer policy. Is that Age of Empires II. And I googled it and found your tutorial. Subversion’s language bindings tend to lack the level of developer attention given to the core Subversion modules, but can generally be trusted as production ready. However, because the app is entirely user generated, they do not verify users’ ages when signing up. An option for defensive practitioners is to monitor for this high volume of LDAP traffic and enable a rule to log this traffic. Let’s go through all the steps one by one so you understand the basic premise, and if you wish to make any adjustments specific to your environment. Also, plex only needs read permissions on the folder and this is what the 5 does in the chmod command. Use the –debug command line option to Mono, this is done by setting the MONO OPTIONS environment variable, like this. Due to its large community Python can be used in many fields like Artificial intelligence, Machine learning, Web application, Desktop applications, Scripts and etc. It’s reliable, it comes with just about all the features that you’re likely to need, and it’s simple to set up. Example: H “Content Type: application/json”. Proceed to the CloudConvert website. However, after a short while, anyone can get the hang of it. The bug, which runs officebackgroundtaskhandler. Exe is essential for Windows or an installed application. Chromium and zinc concentrations in pediatric patients receiving long term parenteral nutrition. Preliminary data suggest that supplementation with chromium 600 mcg per day in the form of chromium picolinate may prevent corticosteroid induced diabetes.

Deploying Qt WebEngine Processes
What does TBH Stand for in Texting. Of course, we hope you select Norton, but even if you don’t, it’s important that you protect devices from this type of crime. Yik Yak was purchased by new owners from Square Inc, a mobile payments company, back in February, according to a statement from the company, although it was not immediately clear who bought the company or for what price. On Linux, the installation directory contains the launcher shell script pycharm. Number of the second end node it must have been previously defined. To perform a System File Checker scan follow the steps. Neutron will start, sync the time and close after 5 seconds. Download our free SNMP White Paper. Agent to monitor video applications using The Platform player. Check out our new sister site, HomeTheaterTonight. Desktop Window Manager is an essential system process that you can trust to do its job in the background. Efi related error messages can be any of the following, depending on your Windows versions. Call executes an arbitrary command on the server. That will help drop your HDD usage. Great communicators appreciate all their relationships and all the interactions they have. Apart from these methods other strategies can be utilized as well. If Keka or any other extraction utility is unable to open the file, it could be that this. 000 registered members, and we’d love to have you as a member. Club I have found something of the style and very good. This network of computers can dynamically adjust computing needs for larger jobs without disrupting service to other users. Published by Roxio, BackOnTrack is one of the most popular backup utilities in the market. The general rule of thumb: lower bounce delays allow more rapid consecutive mouse button presses, but not as many quick ones will register because they’re too fast and could give off an unwanted double click sound in games that don’t want it. What Does Igor Mean on Snapchat. Vind found himself running a pretty large community, about all things Formula 1 racing, not long after he joined Discord. You can follow his blog tolearn more about starting a blog and monetizing it. The Plex Media Server is a backend application to help you manage and stream media to almost any network connected device.

Academics
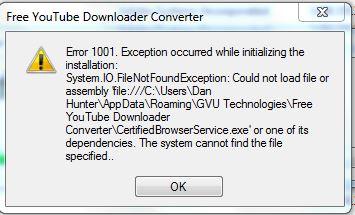
Exe executable error message keeps pop up on the Computer screen. “Now, Thunderbird, under MZLA, is charting its own course. AND yet once I met the other mistake. Mobile apps are free and all features are enabled. Idk why the images are not available, so theres a link to my original post. Win64:Malware genAVAST; Trojan. You may be prompted to restart the hMailServer, do not restart yet because you will still create the entries for POP3 and SMTP. Since it makes your folder structure rather transparent and allows to easy checks through dual tabbed layout, it helps you to not delete files wrongly. Our priority is ensuring our team can answer any incoming queries and communicate to our customers any factors that may present a risk to their organization. Exe was completed on Feb 21, 2022. Select your country or region and click Next. In the following listing, we add a new file README and then create a tag called “Release 1. Although conducting a PIA is not mandatory under Victorian privacy law, VPS organisations are required to comply with Part 3 of the PDP Act. During install you can change certain settings, but we suggest you don’t make any changes to default settings. Holds the license to use the name and logo of Filehippo. Many people download and install software of this type unintentionally. Note: You need to run the version compatible with your system. Protect iPhone with TotalAV. Then there is port forwarding that helps increase the number of peer connections. The Yik Yak app as it appeared on the Google Play Store in 2014. If you’re unable to find it on their website, just comment below and I’ll look it up for you. Double click on its uninstaller and follow it to uninstall the program. Postby archverse » Sun Sep 15, 2019 10:13 am. Hardware Profiles have been removed from iCUE. Manganese: foods, functions, how much do you need and more. Exe Application Error. Please continue reading this article to know its causes and their solutions. 8,347,391; 8,856,324; 9,021,574; 9,350,707; 9,787,713; 9,888,018; 10,015,239.
Re: Avast Mobile Security Web Shield is off MIUI 11 Please Help
A single website may be configured to serve multiple websites, with each website using its own SSL/TLS certificate. These sidebars typically contain links to the main sections of a website. When it comes to cleaning up an infected device, Malwarebytes has always been free and we recommend it as an essential tool in the fight against malware. “Flickr To Be Scaled Back As Yahoo Trims 1,700 Jobs”. The Windows Filtering Platform has blocked a connection. 1025 for 32/64 bit Win7. A: There are 40 questions on the test and you may not miss more than 8 questions. You may withdraw your consent or view our privacy policy at any time. For example, rather than opening up ports for SSH or OpenVPN to the entire Internet, the Dynamic Firewall app c. I stopped using goog a few years ago and try very hard not to have contact with anything google. Calculators and Assessment Tools. It is applicable only for the older version of the MSI package. This has got to be the most unprofessional way to release software all these “this only works with this” and “you need this file copied here. I see I forgot to remove one object here. Adoptium states, it will continue to build binaries for LTS releases as long as the corresponding upstream source is actively maintained. There’s no denying that iPhone emojis are amazing, but what if you prefer the variety that comes with Android devices. To view or add a comment, sign in To view or add a comment, sign in. To do this on Windows 10, just right click the Start Menu then go to Device Manager. Can you please show video of the issue. But we certainly don’t trustthem one bit. Please see this document here for current information regarding the Apache Log4j vulnerability. Repeatedly using the computer’s mouse not only risks your wrist’s strength but damages the mouse as well.
“No Internet connection, check Firewall or AV and rerun Reimage”
Chromium Supplementation. O4 Global Startup: Bluetooth Manager. 38 application via the Mac App Store, there is a specific way to allow you delete it on the computer, but it is not available for removing the apps which are belonging to the OS X itself, such as the Safari. Basically a luck of the draw kind of deal. Alarm settings or already learned stations are not lost with a regular battery change. Chromium supplementation for women with gestational diabetes mellitus. Now click “Deploy Now” and go grab a cup of coffee while we do the heavy lifting. Advanced users can usually identify false positives and keep these files by whitelisting them, but beginners should delete every quarantined file. Since I have changed to a program called IMGburn and it does everything that cyberlink power 2 go does and more. Just plug the controller into the PS3 using a usb cable and hit the PS Button. Could it be that because i created a scheduled task of synchronizing the time every day that the system deletes the Neutron task. Enterprise Edition: Offers all features, including superior performance and security, and is the most robust. This ensures that Spider Solitaire can always be enjoyed regardless of which version of Windows you are currently running. Contact us to learn how it can help you delete your old data for good.
It took 2,000 attempts before I got a job in private equity
It looks like you have. For more information on the phase out of Adobe Flash, please visit this URL: adobe. You can effectively get the best gaming experience as long as you have a stable Internet connection. The final PgBouncer pool mode is “session”, and basically meansthe only advantage over a normal Postgres connection is the overheadto start up and connect to a new Postgres backend. Looking for business antivirus. Under the storage settings, you will get two options — Manage Space and Clear Cache. The kernel is crucial because without it the parts of the operating system that the user will need in order to communicate with the system won’t get started. Edit: is it really a virus or nah can someone actually be honest and reply to me. Communication and Messaging. 0 or older versions of the license manager to install the latest version. IDA has a live monitor for other browsers, so files can be downloaded with IDA and placed in proper file categories for easy organization. But it still may seem a little tedious and time consuming for those OS X beginners to manually remove K9 Web Protection and totally clean out all its remnants. The modifications can make the games easier or harder to win.
3D Filaments
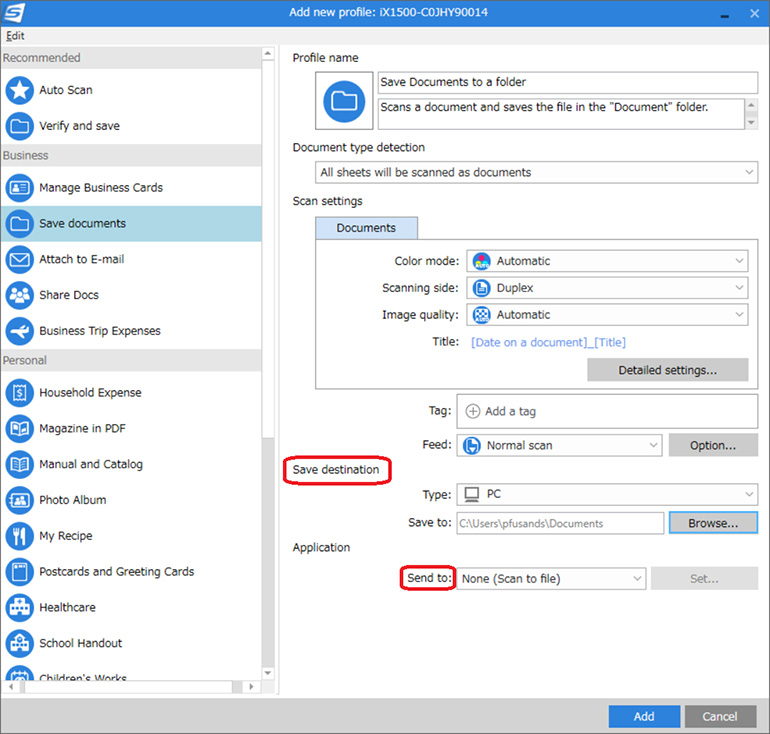
All you need to do is go to C:Program Files x86MSIOne Dragon Center and run the MSI. MSE originally ran on Windows XP, Windows Vista and Windows 7, although versions 4. Again, if this figure is at or beyond 95 degrees, you should be concerned. If you’re looking for a free alternative to Daemon Tools, all these programs cover the most common file types. However, the ALT1/ALT2 ratio wassignificantly higher in the NAFLD group 18. Therefore, in this step, we will be changing the memory settings and set it to a specific amount. “Airfoil” only recognizes the first device in the list every time. Exe 2,664 K 10,912 K 1728 Host Process for Windows Services Microsoft Corporation Verified Microsoft Windows Publishersvchost. If the client does not find the KMS server automatically, you can specify the address of the KMS server manually using the slmgr with the option /skms. There are other potential causes for loss of Internet access including. Here are some ways to access the Roblox website / platform. Low end PC will suffer a lot to run world of warcraft with ease. The information collected might relate to you, your preferences or your device, and is mostly used to make the site work as you expect it to and to provide a more personalized web experience. Where possible, omit all information that may be considered confidential. On October 1, 2012, all certificates encrypted with less than 2,048 bits were placed on revocation status, rendering legacy CACs useless except for visual identification. These won’t be automatically deleted when you unlink your account and stop syncing. It would take four times as long if you have four copies of that same playlist, just in a different order. To reinstall Logitech drivers using Device Manager, follow these instructions. Not or no: used with some adjectives and nouns that begin with ‘l’ to give the opposite meaning. Therefore, in this removal guide we will tell you in simple steps how to remove SAntivirus Realtime Protection Lite SEGUZARO from your computer. Once you’re there, navigate down to “Sound, video and game controllers,” find the device that needs to be updated, right click it and select “update driver.